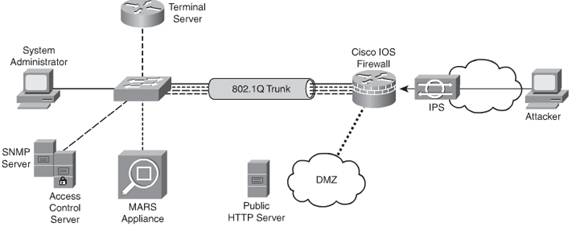
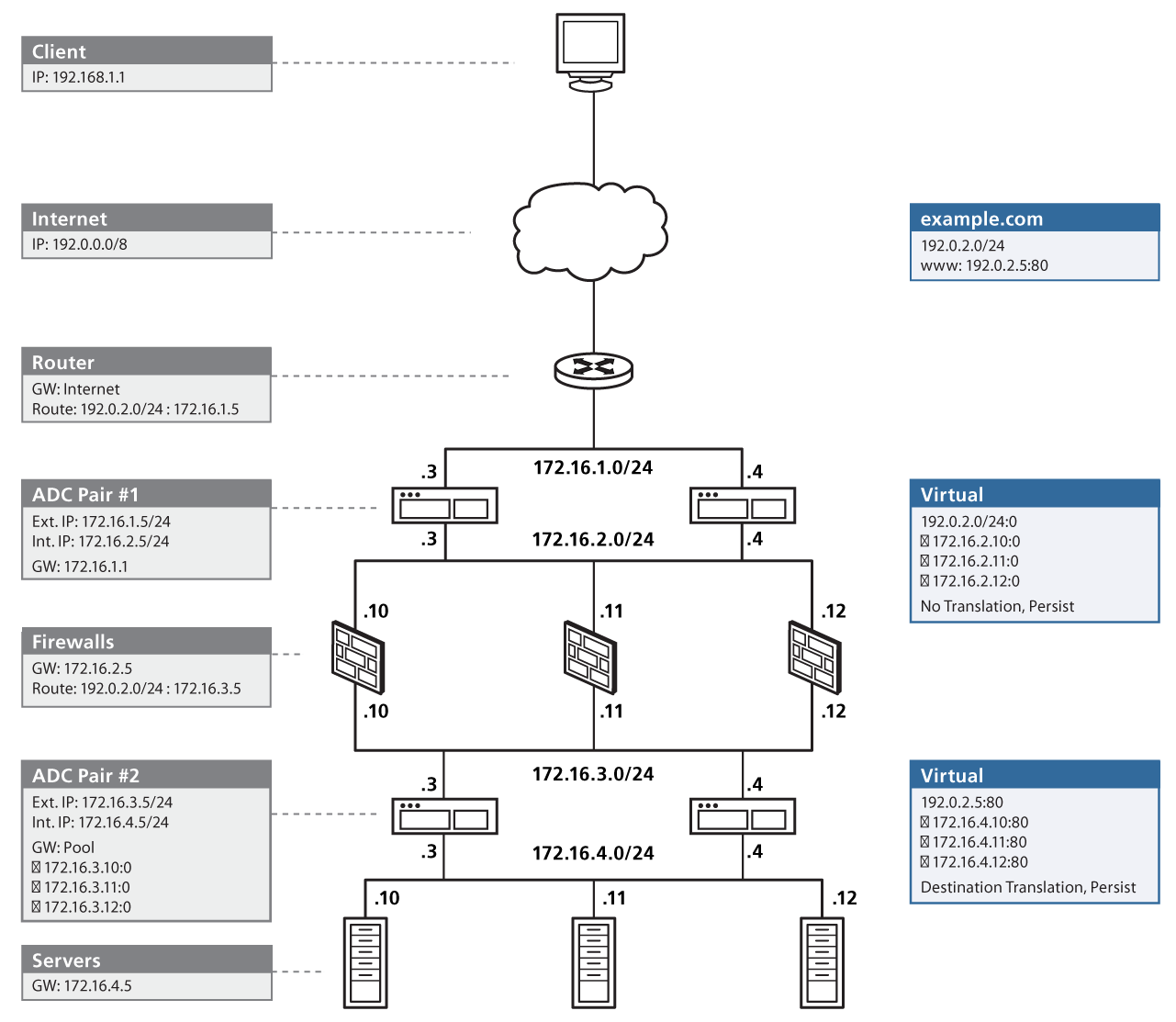
Network Based Firewall Examples

A firewall that filters ip traffic between apair of bridged interfaces.
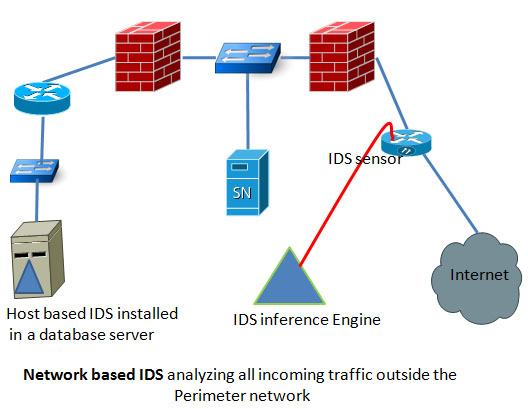
Network based firewall examples. The network based firewall is usually a dedicated system with additional software installed to monitor filter and log traffic. The host based firewall can also be configured to the particular computer where customization can make the firewall more effective. This is a dedicated server with proprietary firewall software installed. A classic example of host firewall is the windows firewall which comes by default in all windows operating systems.
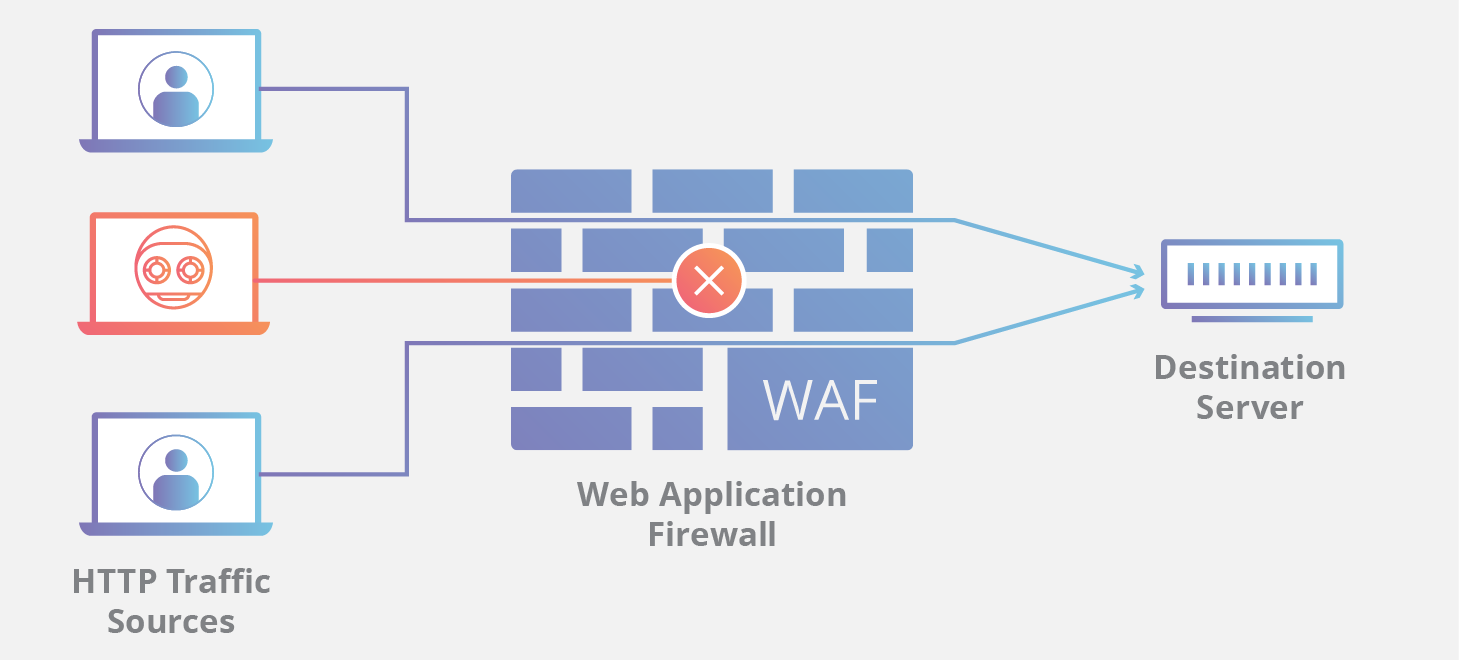
Network firewalls guard an internal computer network against malicious access from the outside such as malware infested websites or vulnerable open network ports. Modern versions of network based application firewalls can include the following technologies. For example a popular network based firewall used in many larger environments is sidewinder. Hybrid firewall a firewall that is a combination of the various firewalls types.
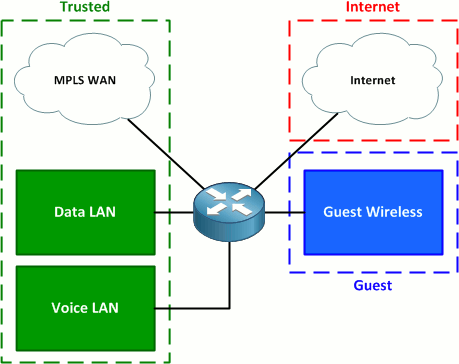
Firewalls have been a first line of defense in network security for over 25 years. For example an application inspection firewall combines a stateful firewall with an application gateway firewall. You can find network firewalls in homes schools businesses and intranets. Several major firewall companies offer a software version of their network firewall.
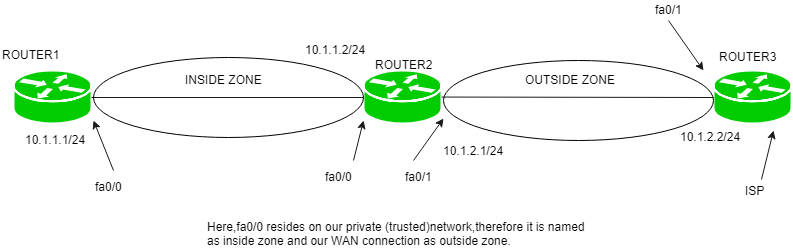
Some companies use host based firewalls in addition to perimeter based firewalls in order to enhance internal security. For example some of the malware attacks that may get past a perimeter firewall can be stopped at the individual device or workstation using a host based firewall. Most operating systems provide a firewall to protect the host computer often called a host firewall. A network based firewall would have two or more network interface cards nics and all traffic passes through the firewall.
A host based firewall setup can also be simpler for some users. A firewall is a network security device that monitors incoming and outgoing network traffic and decides whether to allow or block specific traffic based on a defined set of security rules. For example iptables is the firewall application provided as a part of the linux operating system.